Windows Server 2003 Sp1 Standard Russian Military
Archived Information. Week Radio. Join us for a roundup of the top stories on Information. Week. com for the week of November 6, 2. We'll be talking with the Information.
Week. com editors and correspondents who brought you the top stories of the week to get the.
Top Vulnerabilities in Linux Environment. It is generally stupid to talk about individual vulnerabilities without taking into account the.
Fix Most Windows Errors and Problems With Tweaking.Com Windows Repair 4.0.2 (Major Update) Video: Using Tweaking.Com Windows Repair to Fix Windows Problems. If you have architecture flaws like those in Hillary email server you are royally f*cked no matter how hard you try to patch individual vulnerabilities.
- The version 16 release of FTP Voyager provided a "next generation" FTP client built with 64-bit operating systems like Windows® 7 and.
- UpdateStar is compatible with Windows platforms. UpdateStar has been tested to meet all of the technical requirements to be compatible with Windows 10, 8.1, Windows 8.
- MS Paint, the first app you used for editing images, will probably be killed off in future updates of Windows 10, replaced by the new app Paint 3D. Microsoft lists.

InformationWeek.com: News, analysis and research for business technology professionals, plus peer-to-peer knowledge sharing. Engage with our community.
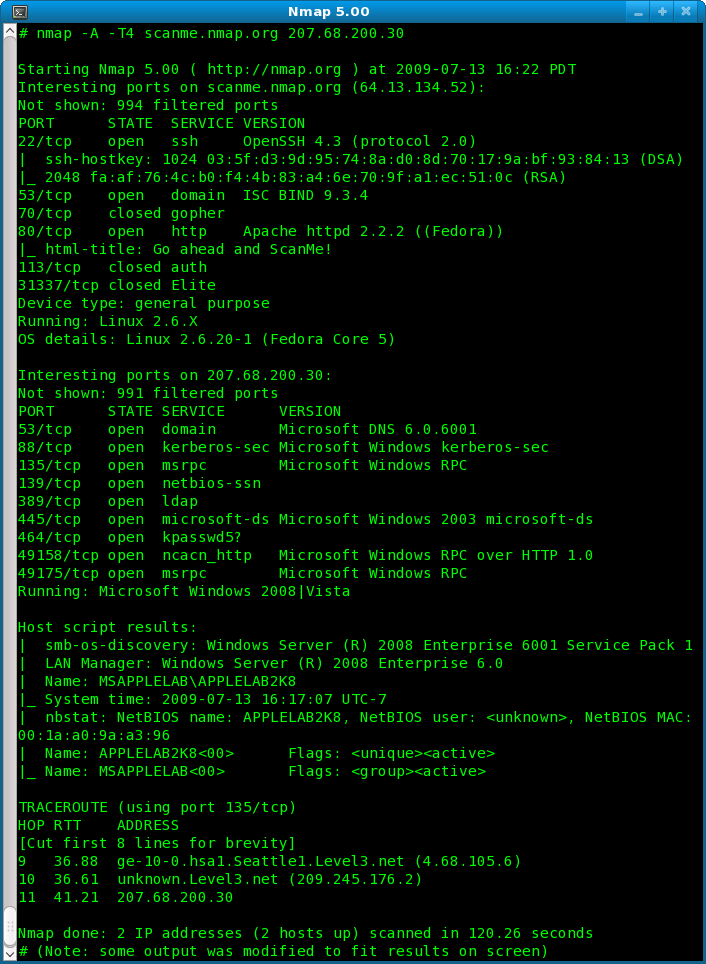
Also routers, switches and even network printers can be as vulnerable or even more. Aspen Pinch Software Free Download. Linux servers or desktops.
Internet routers are common point of attacks. Usage of proxy servers for internet access now is considered to be. With recent examples from. Hillary Clinton email scandal it is also clear that shadow.
IT represents a significant and underappreciated danger. Note that the level of qualification of. NIST recommendations were ignored in. Theoretically this is true, but the complexity of open source software negates this. According the US Government. And this is not surprising as Linux.
RHEL). This count removes duplicate reports. Linux or Windows. In March 2. 00. 4, Forrester Research. Linux is no more secure than Windows. Also Linux if often running. It is true that Windows is often used is less secure way then Linux (with the user operating. Administrator account or equivalent), but if regular user account is used such mechanisms for providing security.
Windows Group policy and cryptographically signed executables beats Linux in default. An excellent security system introduced by Suse. App. Armor did not became Linux standard. Red. Hat SElinux that few people understand and few configure correctly (most often disable) is dominant. Only Solaris is competitive in this area. Another key factor that the.
OS. is the most natural target of attacks. Some market exist for Linux too. There is no such market for. Solaris. There is also government sponsored hackers who develop professional exploit for both windows and. Linux. They can be captured disassembled, studied and replicated on a new, more.
In other words when we discuss security of an individual Linux box this is an abstraction, and often not very. What we should discuss is the security of network in which particular Linux box.
As. such they represent more subtle and potentially more lucrative way to break into the server the. There are a lot of commercial servers, even in major datacenters which still have. DRAC or ILO, and default accounts still enabled. Which ports are opened across the segment on this sensitive. Is DMZ configuration used. Is private DNS used?
Patching is another. And patching infrastructure can and was in the past.
Again look at the level of stupidity in. Hillary bathroom server (Hillary.
Clinton email scandal) as a pretty educational example how not to do such things. Smartphone infrastructure (and Android is nothing but a proprietary version of Linux used by. Google) in companies is now another . Here stupidity and gullibility of users reached probably. That. somewhat guarantees that for the next few hours you work with . There is no real necessary for such directories as /bin /usr. And /etc/while writable consist mostly of static files.
And then there is such danger as Shadow IT, which often. IT environments. And all this mess was maintained by rank- and- file specialists with mainly. IT for non- profits and without proper security training. After this episode it is easy to stop believing into the ability of the US government to maintain. The server (or group of servers ) was configured without any attempt to satisfy NIST guidelines for this type of servers. If you have. architecture flaws like this, you are royally f*cked no matter how hard you try to patch individual. Architecture faults overwrite all this and when we are talking about individual.
Otherwise the whole discussion just does not. Architecture faults overwrite those efforts and when we are talking about individual. Otherwise the whole discussion just does not. It claims Linux, in this particular sense, was less secure than Windows because. Linux outnumbered those for Windows, but also because time for fixing it was not impressive.
Also. with firewall tightly configured many of them just does not make any sense and are not exploitable. On high level. of security with App. Armor enabled (or if you have an. SElinux security, able to configure it properly for your case) and with internal firewall. Only very few protocols that are opened (DNS is one example). But even for DNS there are inventive way to improve security - - for. DNS tables are pretty much.
CD instead of hard drive. That makes it harder possibility to modify them.
DNS server to this folder - - the. Another important aspect is what you are running.
For example if you do not run X server, it is unclear. In this sense. minimization of your installation is the most powerful security tool and early hardening packages. Titan provides some minimization frameworks. Now most commercial distribution have the option.
Now most commercial. Linux distribution have the option . But the way how Linux is typically installed often deny or even pervert this advantage. In June 2. 00. 4, Danish security firm Secunia. Windows was more secure, than many people think. And march larger.
During this same time, vulnerabilities. Microsoft products numbered seven, or about one in four of all advisories. The Aberdeen Group says this information proves that Linux and UNIX are just as prone to Trojan horse. OS, despite press reports to the contrary. According to the Aberdeen Group, the. The group says that the open- source software and hardware solutions need.
As I. mentioned before, it is. SSH implementation was for several year the preferred way of hacking into. Linux ISPs. We can rail against Microsoft and its security policies (which are indefensible), but far more people and systems use Microsoft's.
And most Linux system administrators do not know how secure Linux. Linux is moving to. Windows environment when . And this. environment that can't be defended by any technical means. Moreover even despite the fact that Linux isn't as prevalent as Windows, we're still seeing a.
Linux security advisories from year to year. We judge that the large companies. Linux on DMZ and deploy Solaris instead, if they are really. Linux security. Security via obscurity is not a bad thing. Even. use of Free. BSD (or, better, Open.
BSD) sometimes can dramatically improve the level of security, as it automatically stops. Long time ago, Secunia publishes graphs on the security. Red Hat Enterprise AS3. According to the graphs, 6. Even. if they are wrong by 5. Another. graph shows that 1.
According to these. Windows 2. 00. 3 vulnerabilities can be exploited by a remote user, which taking. Linux and windows are.
None is superior to another. The number of vulnerabilities that allow a cracker to escalate. Windows compared to 1. Red Hat, which also means that they are close. That means that without additional hardening Red Hat Enterprise Server AS3 used to have. Windows 2. 00. 3 Enterprise Edition.
In other words the level of security of the system depends on several factors: General architecture of particular network (whether NIST recommendations were used to. App. Armor is. used and properly configured (brilliant security idea that never get enough traction as Red Hat. SElinux), whether organization uses private DNS, uses hostfile for name resolution. DNS (not a bad idea for small networks), how well individual server is hardened. Qualification of administrators and users. Level of security of other components of particular network segment (DRAC or ILO if they are. It means that it is almost meaningless to discuss it in abstract terms, It should be self- evident that the most serious type of vulnerability.
Internet both on Windows and Linux. Especially for the. I actually saw that UUCP. The most secure way to use computers is to use isolated non- network computers producing CD/DVDs. Rescanning of printed documents is pretty accurate, especially for regular. While there is a non- stopping stream of remotely exploitable Linux vulnerabilities.
But for the top vulnerabilities it make sense to go extra mile. Restricting IP range via tcp. As. they typically they do not understand what they are doing this is just noise, but still it. URLs unique for the site. You should never have.